Website owners love WordPress. So much so that around 40% of them have picked it as the basis for their online projects. Yet, you might be surprised to find that some people are not too sure about how the world’s most popular Content Management System (CMS) works.
Perhaps more worryingly, they’re concerned about some aspects of WP’s security, more specifically, the mechanism for hashing users’ passwords. Let’s explore the area in more detail and see if the criticism is founded.

What is Hashing?
As a website owner, it’s your responsibility to protect your users’ data from hackers. Storing their passwords is an important part of this.
Imagine that hackers manage to break through your defenses and steal your website’s database. It’s already a nightmare scenario as, depending on the type of service you offer, your database may be full of sensitive information.
However, it could get a lot worse. If you store users’ passwords in plain text, there’s absolutely nothing to stop the hackers from exploiting them.
We all know that people reuse the same passwords on multiple different accounts. If criminals decide to try the stolen credentials against other online services, they are more than likely to successfully break in. A single breach could lead to the compromise of tons of data.
The purpose of hashing is to contain all this. Hashing is a cryptographic function that turns text into a scrambled string of letters and numbers called a hash.
When a user picks a password, the web application passes it through the hashing function before storing the resulting hash in the database.
The next time the user tries to log in, the password they enter goes through the same mechanism, and the hash is compared to what is stored in the database. If it matches, the system lets the user in. If it doesn’t, the website returns an error.
There are online generators that can illustrate what a WordPress password hash looks like. Below you can see the hash of “Password123!#” according to Code Beautify’s generator.
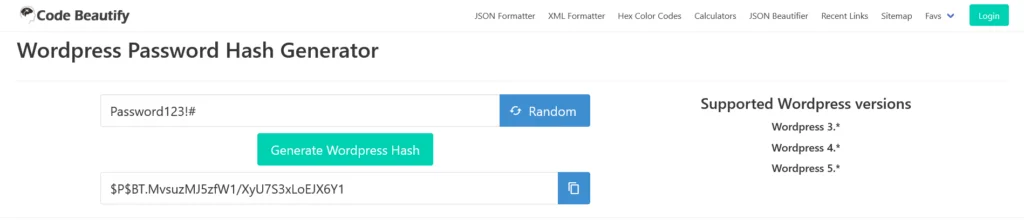
The crucial thing about hashing is that it’s a one-way function. In theory, it should be impossible to reverse the process and derive the plain text password from the hash.
However, as is often the case, theory and reality don’t match.
There are many different hashing algorithms, with some offering better security than others. As hardware evolves, hackers’ brute-force attacks become more and more powerful, and we’ve reached the point where only a handful of algorithms are considered strong enough to properly protect users’ passwords.
You may need some help to understand how much stronger some hashing mechanisms are than others. To illustrate the differences, experts like Jeremi Gosney often simulate various attacks against popular hashing algorithms and share the results during events dedicated to password security.
In 2012, Gosney used a cluster of GPUs to launch a brute-force attack against simple implementations of several hashing algorithms. We’ll now summarize the results for three of the most popular mechanisms.
During an attack on the MD5 algorithm, Gosney managed to make 180 billion guesses per second. With this, he would successfully guess all possible 8-character passwords in a little over 9 hours.
When attacking SHA1, Gosney was making around 61 billion guesses per second, which would have allowed him to successfully guess all 8-character passwords in approximately 27 hours.
When attacking bcrypt, he only managed 71 thousand guesses per second, meaning it would take him in the region of 2,700 years to successfully guess all possible 8-character passwords.
The figures above were recorded with GPUs that are about ten years old now. Modern hardware is much more powerful and can enable even faster brute-force attacks. However, Gosney’s results are as good as ever at illustrating the difference between algorithms like MD5 and bcrypt.
You’d think that WordPress, the world’s most popular CMS, would use one of the more difficult to crack algorithms. You may be in for a surprise.
What Type of Hashing Does WordPress Use?
WordPress initially had a straightforward implementation of the MD5 hashing algorithm. MD5 has one distinct advantage over many of its competitors – it’s extremely quick. However, even way back in 2007, collision attacks against the MD5 hashes took no longer than a few seconds on a regular PC. Needless to say, at the time, WP’s development team was getting a lot of stick for using the algorithm.
Released in 2008, WordPress 2.5 came with PHPass (pronounced P-H-Pass). PHPass is a hashing framework that supports several hashing algorithms, including MD5 and bcrypt. As we established in the previous section, bcrypt is much stronger than MD5, and it’s widely considered the best hashing algorithm for PHP applications.
However, WP’s implementation of PHPass continues to use MD5 to this day. At this point, we need to emphasize the fact that despite being based on MD5, WordPress’s hashing mechanism provides more than adequate security.
PHPass adds cryptographic salts to every single password before hashing it. A salt is a unique piece of data attached to the plain text password before the hashing mechanism is used. Thanks to it, identical passwords don’t result in identical hashes, and the hackers have a much harder time guessing what the user has picked as a password.
Additionally, PHPass makes eight passes of MD5-based hashing and employs key and password stretching techniques that further protect the credentials.
As a result of all this, brute-force attacks against WordPress’s hashing mechanism are impractical. For now, that is.
Why Does WordPress Continue to Use MD5?
Rewind the tape a bit, and you’ll see that implementing a strong hashing algorithm into a PHP project wasn’t exactly a walk in the park. However, PHP 5.5 introduced official support for bcrypt, with native functions for both hashing passwords and verifying them during login attempts.
WordPress’s hashing mechanism does offer sufficient security at this time. Still, many people argue that keeping it as it is makes no sense given the availability of stronger algorithms that can be implemented without too much hassle.
Yet, WordPress’s development team seems strangely reluctant to make any changes to this particular part of the core. The reason for this is backward compatibility.
WordPress maintains its popularity and continues to grow its market share not only because it’s incredibly versatile and easy to use but also because it will run on just about any hosting platform. Far too many people use legacy systems to build new projects, and many existing websites run in woefully outdated hosting environments.
The old software makes these projects sitting ducks for the hackers, so WP’s hashing mechanism is likely the least of their worries, especially considering the decent security it offers. The CMS’s developers know that changing the hashing mechanism could impact quite a few projects, and they prefer not to do it.
It’s an illustration of an “if it’s not broken, don’t fix it” strategy, and you have to agree that, especially in light of the enormous number of people that can be affected, there is some logic behind it.
However, many website owners consider security the highest priority in organizing every single aspect of their projects. For them, using a hashing mechanism based on an algorithm as weak as MD5 just isn’t good enough.
Luckily for them, there are alternatives.
Change Your WordPress Website’s Hashing Algorithm With a Plugin
Thanks to WP’s modular architecture, you can easily change your website’s password storage system.
Search for “bcrypt” on WP’s official plugin directory, and you’ll find quite a few matches. Installing them is a standard, two-click job, and pretty much all of them promise to make the switch from MD5 to bcrypt without telling all users to reset their passwords.
Roots.io, a company creating various WordPress development tools, also has a plugin that enables you to use bcrypt. However, it’s not available on the official directory, so the process of installing it is different. Let’s follow the steps.
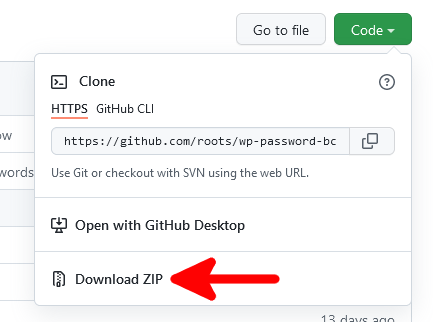
1. Download the plugin from GitHub.
Roots’s plugin is available here. To download it, click Code and then select Download ZIP.
After saving the file on your computer, you need to extract the archive.
2. Create a new directory inside the wp-content folder.
The plugin created by Roots requires the creation of a folder named “mu-plugins” inside the “wp-content” directory. You can do it via SSH, through the file manager in your web hosting control panel, or via your favorite FTP client.
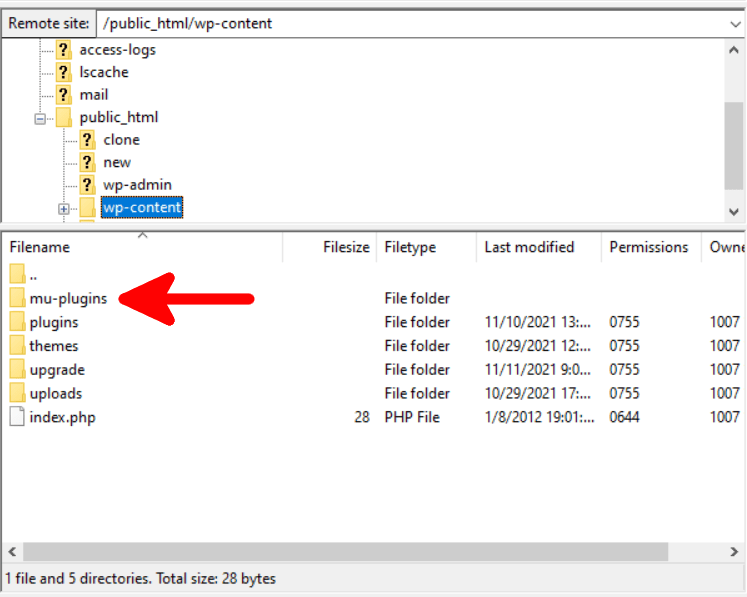
3. Upload the wp-password-bcrypt.php file.
To install and activate the plugin, upload the “wp-password-bcrypt.php” file to the “mu-plugins” folder.
NOTE: You don’t need to upload the entire contents of the archive. Only the PHP file is required.
The plugin will appear in the Plugins > Installed Plugins menu under the Must-Use tab.
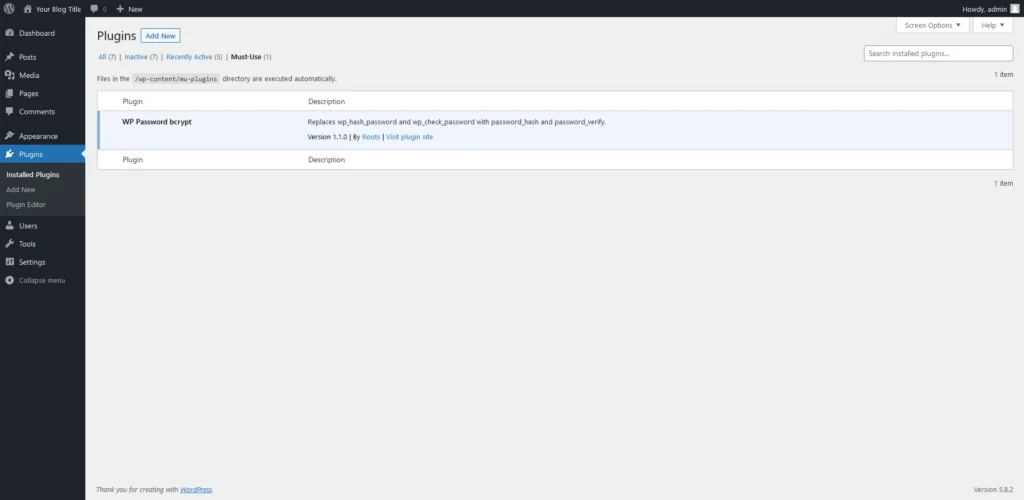
Because Roots.io’s add-on is one of the so-called must-use plugins, it’s automatically activated upon installation, and users can’t deactivate it from the WordPress dashboard.
The only way to get rid of it is to remove it from the mu-plugins directory, so it’s a good idea to use it if multiple people have access to the WP dashboard and you want to make sure they don’t meddle with the website’s password hashing mechanism.
All bcrypt WP add-ons work in the background, and you can’t really expect any different features or functions. However, there are differences in the way the plugins tackle the problem.
Some employ the native PHP functions to hash and verify the passwords, and others re-configure the PHPass framework to use bcrypt instead of MD5. In all cases, you’ll need PHP version 5.5 or newer, which you should be using anyway.
The choice of a plugin comes down to personal preference. If they all look the same to you, be sure to read the reviews and see what people who have used them think.
Conclusion
Although WP’s password storage system isn’t based on the most secure hashing algorithm currently available, there’s no immediate threat to the security of your website and its visitors.
However, WP’s modular architecture and the global community that keeps the project alive means that employing a more sophisticated password hashing algorithm is something you can do with as little as a couple of mouse clicks.
You won’t be wrong in saying that the same architecture and the community make WordPress the most popular website-building application in the world.
FAQ
How are user passwords stored in WordPress?
After a visitor picks a password, WordPress hashes it before storing it in your website’s MySQL database. During a login attempt, the CMS uses the same algorithm on the password the user has entered and compares the resulting hash to what is stored in the database. If there’s a match, the user will successfully log in.
How does hashing works?
Hashing is a cryptographic function that turns your password (or another piece of data) from a human-readable format into a string of letters and numbers that bear no visual resemblance to the original. Hashing was conceived as a one-way function, so unlike encryption, there’s no key that can decrypt the hash and return the plain-text password. However, some weaker hashing algorithms are susceptible to brute-force attacks, and hackers can reverse them.
Is it possible to decrypt passwords hashed by WordPress?
WordPress uses the PHPass framework, which salts the passwords before performing eight passes of MD5-based hashing. Alongside this, there are other techniques that further protect the data.
As a result, although it’s based on MD5, an inherently weak algorithm, mounting a successful attack against WP’s hashing system is not really practical at the time of writing.




